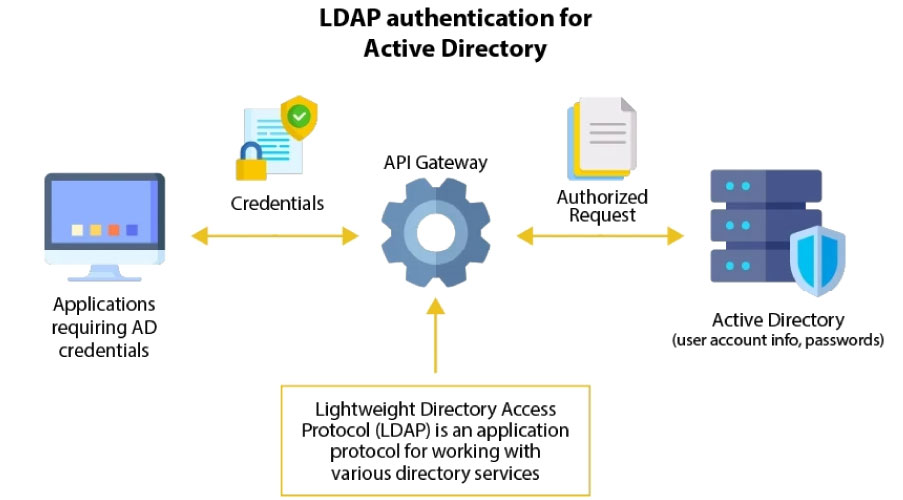
LDAP (Lightweight Directory Access Protocol)
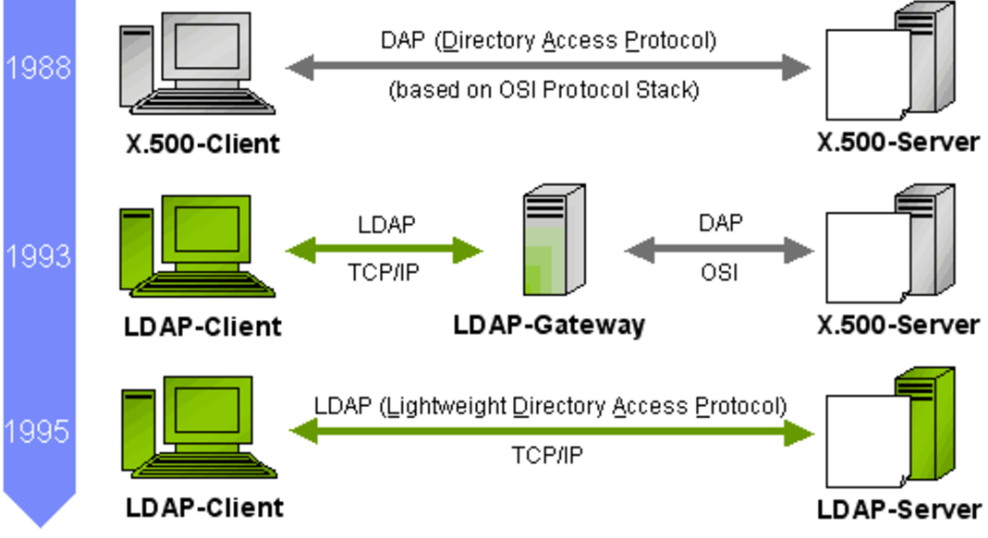
LDAP is a lite version of DAP (Directory Access Protocol) which is a part of X.500. LDAP is used in networks to organize and retrieve information about users, devices, or other resources. It was introduced to overcome issues with X.500. X.500 did not support network-related functionalities, which was addressed with the introduction of LDAP.
Check the image below how lightweight directory access protocol improved and X.500 and DAP (Directory Access Protocol) lose their popularity.
Why Microsoft introduced LDAP ?
- LDAP supports TCP/IP, whereas X.500 uses the OSI (Open Systems Interconnection) protocol which was complex.
- DAP implementations were Complex and less suited for lightweight or internet-based systems.
- LDAP uses less code the other protocol.
A directory helps users locate something within a network. On TCP/IP networks, like the internet, the domain name system (DNS) acts as a directory, mapping domain names to specific network addresses, which represent unique locations on the network. However, users may not always know the domain name.
LDAP allows users to search for individuals, organizations, or resources without knowing their exact location, although providing additional details can improve the search process.
How does LDAP work?
LDAP authentication is based on queries where the user enters their LDAP credentials, and the LDAP protocol queries the LDAP directory to confirm a match with the credentials stored within it.

LDAP Flow Chart
Below are the steps showing how the LDAP flow works:
- Secure Connection: To start, the user installs an LDAP client on their device. This client establishes a secure connection with the LDAP directory using encryption methods like SSL or TLS. LDAP Port number is 389.
- Authentication and Authorization: The LDAP Authenticate and Authorize the users to resources.
- Submitting a Query: It include searching and comparing directory information.
- The user requests something (e.g., finding an email address or connecting to a printer) through an application like an email server or VPN. The application uses the LDAP client to send the user’s username and password to the LDAP server.
- Update: It include adding, deleting or modifying directory information.
- Query Results: The LDAP directory sends back the requested information, such as the email address or printer connection.
- Ending the Session: The user disconnects from the LDAP directory, and the session is closed.
Read How to Configure Setup on Windows Server –https://www.miniorange.com/guide-to-setup-ldaps-on-windows-server
LDAP Vs Active Directory
It’s a common misconception! Many people, including those just learning about it, mix up LDAP and Active Directory since they work together. LDAP is a protocol, while Active Directory is a directory service that uses LDAP among other technologies.
LDAP is a protocol used in Microsoft’s Active Directory (AD) but isn’t exclusive to it. Active Directory is a large database that stores information about users and groups on a network, while LDAP helps access and manage this data over TCP/IP. LDAP is a simplified version of the Directory Access Protocol (DAP), designed to quickly find directory objects like users or groups with minimal information.
Microsoft Active Directory handles user authentication and management, while LDAP specializes in searching for objects within AD or other directory services (It interact with AD to retrieve data, such as user credentials, but it doesn’t perform authentication itself). Think of AD as a huge library and LDAP as the librarian who quickly finds the book (or information) you need, without needing all the details about it.
LDAP Port Number
The default port for LDAP is 389, while the default port for SSL-based LDAP (LDAPS) is 636. However, these port numbers can be changed if needed.
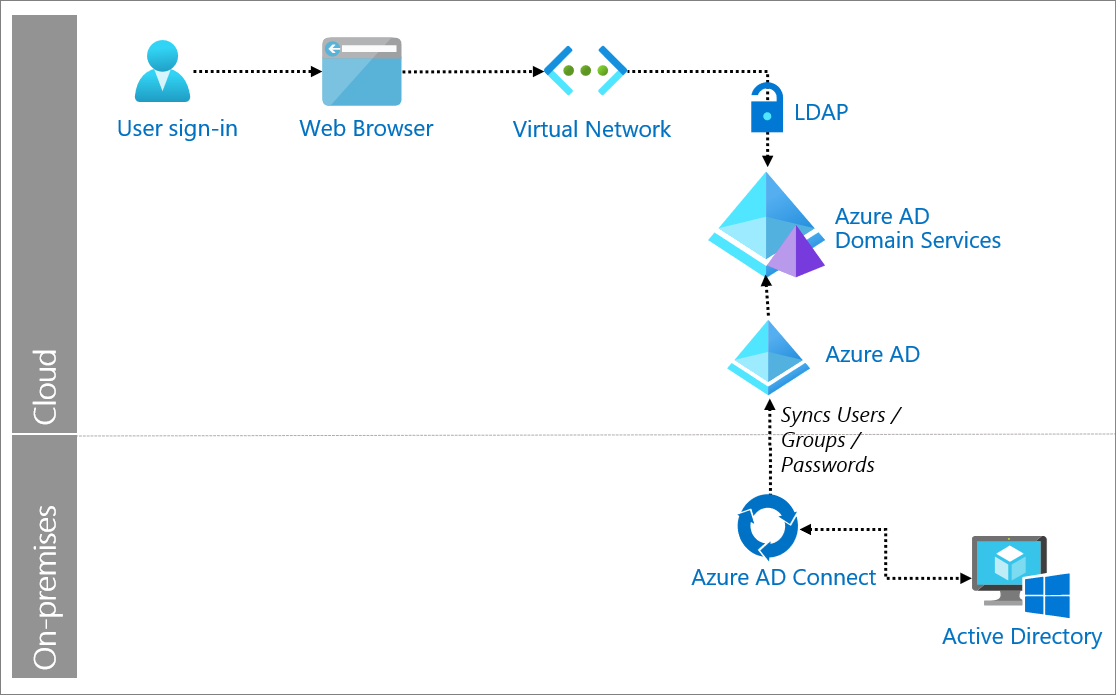
LDAP and Azure AD (Microsoft Entra ID)
Azure AD does not natively use LDAP, but it can integrate with LDAP through synchronization. As a cloud-based service from Microsoft, Azure AD serves as a centralized repository for user identities, enabling access to applications and resources. Azure AD’s synchronization feature transfers LDAP data into the cloud, making the centralization and management of Active Directory resources in hybrid environments easier and more efficient.
What Is an LDAP Injections Attack?
LDAP injection is a type of security attack where an attacker manipulates input fields on a website or application to alter the behaviour of an LDAP query. The goal of this attack is to gain unauthorized access to the LDAP directory, where sensitive data like usernames, passwords, and email addresses are stored.
For example, if a website generates an LDAP query using user-provided data (such as a username and password), an attacker might insert malicious code into the input fields to modify the query. This could allow the attacker to bypass authentication, read or modify sensitive information, or even gain full control over the directory.
To prevent LDAP injection, developers should sanitize user inputs, restrict allowed characters, and implement security measures like multifactor authentication.
Also Read: Difference between Server OS and Client OS
LDAP FAQ
Can LDAP work without Active Directory or non-Windows systems?
Yes, the LDAP protocol can be used to access and manage directory services on platforms other than Windows, such as Linux, AIX, Solaris, and HP-UX.
Does LDAP work without LDAP server?
No, LDAP cannot work without an LDAP server. LDAP is a protocol designed to access and manage directory data, and it requires an LDAP server to store and provide that data. Without a running LDAP server, there is no directory information to query or manage using the LDAP protocol.
What is the LDAP “Distinguished Name” (DN)?
A Distinguished Name (DN) is a unique identifier for an entry in an LDAP directory. It specifies the location of an object in the directory hierarchy, similar to a file path in a file system. For example: uid=john,ou=users,dc=example,dc=com.
How can we secure LDAP?
Below are the steps to make LDAP secure
- Encrypt Communication: Use LDAPS (LDAP over SSL/TLS) to ensure that data exchanged with the directory is secure.
- Restrict Access: Set access controls to limit who can query or modify the directory.
- Strong Authentication: Implement methods like multifactor authentication to enhance login security.
- Monitor Activity: Regularly audit LDAP queries and logs to detect and respond to suspicious actions.
How can we secure LDAP?
Here are some popular LDAP Protocols
- OpenID Connect (OIDC)
- OAuth
- RADIUS (Remote Authentication Dial-In User Service)
- Kerberos
- Apache Directory Server
- Central Authentication Service (CAS)
- Google Workspace Directory
- Amazon Cognito
- Keycloak
- JumpCloud
- OpenLDAP
LDAP Simplified: Final Recap
We Learned what LDAP (Lightweight Directory Access Protocol) is and how it works in managing directory services. Explore LDAP servers, authentication, and the key differences between LDAP and Active Directory. Understand LDAP and LDAPS port numbers, secure communication, and LDAP directory management on Windows. Discover how the Active Directory LDAP protocol operates and tips to prevent LDAP injection attacks.